Internet and web-browsers is a wonderful technology that has revolutionized how information can be accessed in a way that was unthinkable just a few years back. Unfortunately, security solutions have not progressed in the same pace. An example of this are Internet credit-card transactions that essentially is just a copy of the manual methods introduced some 30-40 years ago! This white-paper addresses another problem that so far has not gotten an acceptable solution: How representatives from one organization can authenticate to partner organizations' web-servers. The following picture shows how the majority of such systems work today:
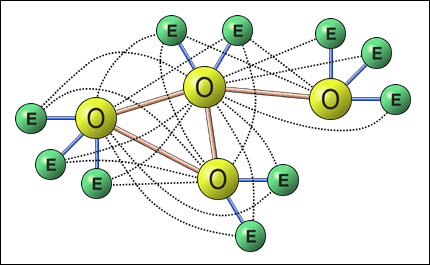 |
| Current Extranet authentication misery. E= Employee with browser
using different |
The current solution deployed by most organizations is to let individual
representatives authenticate to partner web-servers using the "classical"
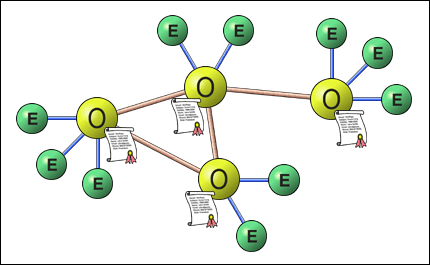 |
| The Purple(tm) objects. E=Employee with browser, O=Organization with server & certificate |
The corner-stone of the Purple(tm) concept are organization-servers equipped with organization certificates (and associated private keys), serving as the true digital equivalents to signed company papers (which has been the foundation for trust in business messages the last 200 years), rendering a single, non-forgeable, business partner electronic identity for all external "e-operations" ranging from authentications to purchase orders . The net result is a perfect blend of security and convenience!
The following shows some of the unique features of Purple(tm):
| | X-OBI's powerful Purple(tm) web-server plugin-components available in both COM and Java® flavors, enable web-developers to apply full PKI-security to critical extranet applications with the same ease as connecting databases using ADO or JDBC by encapsulating the complexities of PKI such as digital signatures and by speaking XML |
| | Purple(tm) dramatically reduces the need for multiple external security solutions by specifying a unified security solution between organizations, while allowing local client security solutions to develop in their own pace at each partner organization. This is actually equivalent to the field-proven security architecture already deployed by the Internet-banks! |
| | For the end-user, Purple(tm) reduces authentication to a partner organization's server, to clicking on a link on the user-organization's Intranet |
| | Purple(tm) preserves privacy and company secrets by only requiring individuals to be fully identified by their own organization (applies primarily to B2B-systems) |
| | Purple(tm) supports full traceability of all external organization-to-organization actions including authentications |
| | Purple(tm) optionally exchanges updated customer information during authentications to mutually keep customer registers automatically in sync. |
| | Purple(tm) is 100% compatible with organizations' current intranet client security solutions - There is nothing new to install, distribute, or configure |
| | As Purple(tm) "tickets" are automatically distributed, on-demand created, XML-based certificates, tailored for each business relation, activity, and individual, as well as eliminating revocation checks by making tickets short-lived, deployment is greatly simplified for all involved parties compared to running CAs and distributing individual client-certificates for every type of business relation |
| | Due to the fully distributed [autonomous] administration of users and business partners, Purple(tm) is extremely cost-efficient compared to current extranet solutions. Becoming a purchaser can often be reduced to setting a check-box in the local staff administration system! |
| | Being from the beginning designed with ASP-operation in mind,
Purple(tm) enables efficient usage by organizations that do not have the
resources or expertise required to run secure servers
|